How to Stop WordPress Brute Force Attacks (2026 Guide)
Are you confident your login page can resist WordPress Brute force attacks? If you run any kind of WordPress website, whether it’s a simple blog or a large WooCommerce store, you are a constant target.
Brute force attacks are simple yet highly effective digital attacks where hackers use automated tools to guess your login credentials thousands of times per minute. They don’t need advanced skills; they just need consistency and speed. In 2026, these attacks will be more common and faster than ever, making them one of the biggest threats to your site’s security.
For this post, I will provide you with a step-by-step plan to block repeated login attempt threats, once and for all. I will show you the most effective defenses and how I make use of the best WordPress brute force protection plugin, LoginPress, to implement every vital security layer.
WordPress Brute Force Attacks (TOC):
What Are WordPress Brute Force Attacks?
A brute force attack is basically an automated bot attempting every single key on a large key ring until one opens the lock. The goal is to guess your username and password, giving them full access to your site.
Here’s a simple breakdown of how this happens:
- The Attacker Uses Bots: Hackers don’t sit there typing; they use powerful software programs (bots) that can input credentials much faster than any human, often hundreds or thousands of attempts per second.
- They Target Common Names: The bots begin with the most common usernames, such as “admin,” “test,” or the site’s name itself, and combine them with detailed lists of leaked or frequently used passwords.
- They Slow Down the System: Even if the password isn’t cracked instantly, this rapid-fire guessing can slow your website down and drain your server resources. It can lead to poor performance for your fair users.
Why WordPress Sites Are Common Targets
WordPress faces an average of 90,000 attacks per minute. This statistic may seem like a lot, but hacking attempts typically target WordPress sites more. This is because of two main factors:
- Popularity and Scale: WordPress powers over 43% of the internet. Because so many sites use it, hackers only need to find a single, successful attack script to use against millions of targets.
- Known Entry Points: Every default WordPress installation uses the same login page address: /wp-login.php. This common entry point makes it easy for bots to start guessing immediately.
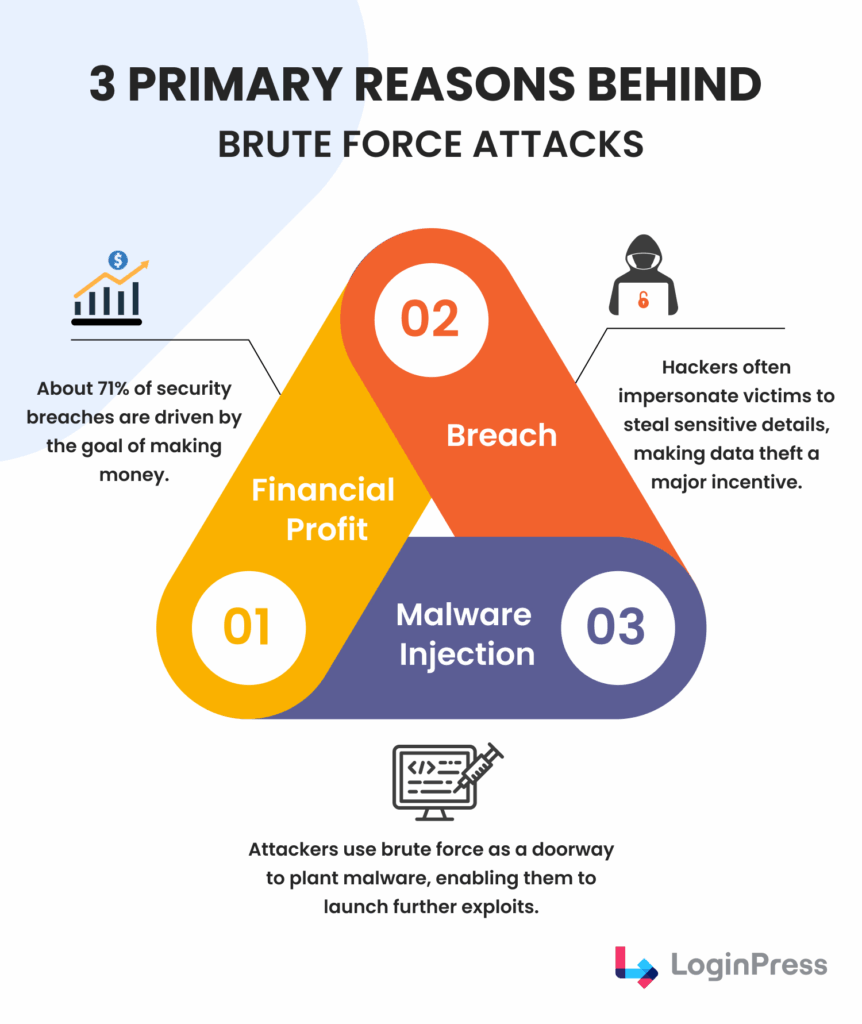
If you don’t take steps to block repeated login attempts in WordPress, your site is guaranteed to be constantly under WordPress brute force attacks.
Effective Methods to Prevent Brute Force Attacks
To effectively stop WordPress brute force attacks, you must implement a strong, layered defense strategy. Think of it like building a house: you need to prevent, restrict access, and enforce strong internal rules. I focused on three core defense methods in this section for your ease.
Method 1: Hide and Obscure
The goal here is to make your website an unappealing target for automated scripts. This helps to block repeated login attempts in WordPress.
- Change Default Usernames: The single easiest step you can take is never to use the default “admin” username. Bots know this name and will try it first.
- Hide the Login URL: Every bot knows to look for /wp-login.php. By changing this path to something custom (known only to you), you instantly block 99% of brute force traffic.
Method 2: Limit and Block Attacks
This strategy focuses on stopping the bot once it finds your login page and attempts to exploit it by WordPress brute force attacks, while tracking the failed attempts.
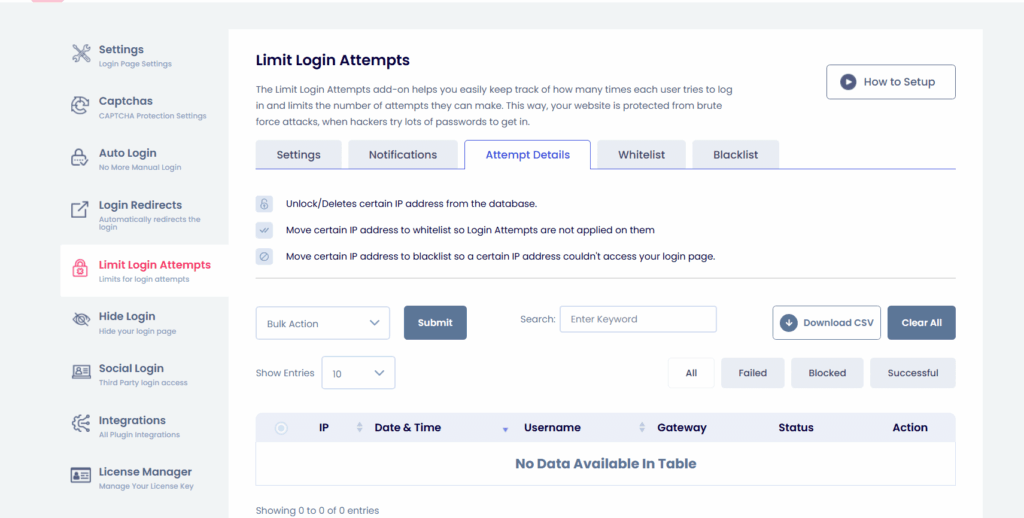
- Limit Login Attempts: Since bots rely on unlimited, high-speed guessing, you must restrict the rate of login attempts. This feature in LoginPress Limit Login Attempts Add-On automatically locks out an IP address after just a few failed guesses, forcing the bot to move on.
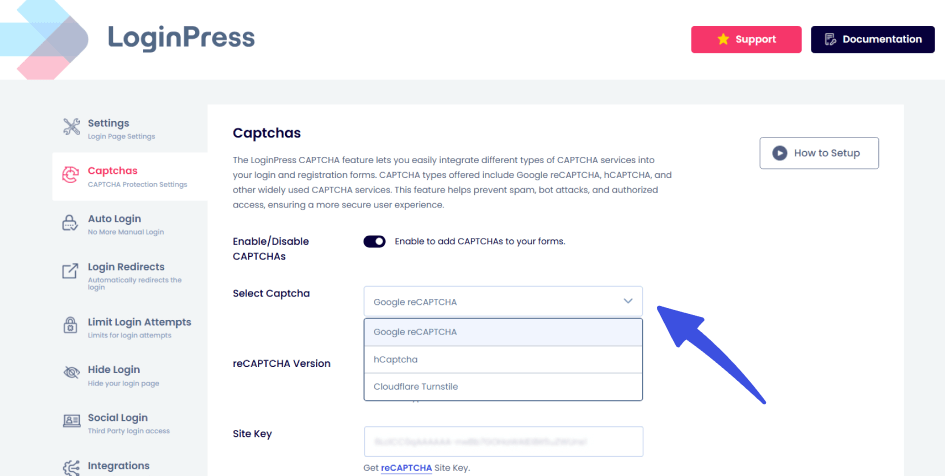
- Use CAPTCHA: Almost 40% of all internet traffic is non-human, so putting up a CAPTCHA on your WordPress login form will help protect your site. LoginPress offers various types of CAPTCHA to users, allowing them to add them to their login forms to ensure that only genuine human users can proceed.
Check out our in-depth tutorial on How to Add CAPTCHA to WordPress Login and Registration Form.
Method 3: Core Protection
These are WordPress security best practices that provide stability even if an attacker manages to bypass the first two layers of defense after WordPress brute force attacks.
- Enforce Strong Passwords: While you can use tools like LoginPress to enforce passwordless authentication using Social Login Add-On, any existing accounts must use credentials that are long, complex, and unique. Weak passwords are the target point for attackers of any system.
- Enable Two-Factor Authentication (2FA): Two-factor authentication (2FA) is one of the most effective layers of protection when using passwords. Even if a hacker successfully guesses your unique username and complex password, they cannot log in without the second, temporary code generated on your personal mobile device.
There are several WordPress 2FA plugins on the market. To help you decide which one works best, you can check out a detailed comparison of the 7 Best WordPress 2FA Plugins in 2025.
LoginPress: All-in-One Brute Force Protection Plugin
As I have discussed in the earlier section, protecting your login from WordPress brute force attacks requires multiple methods. Instead of installing separate plugins for hiding your URL, adding CAPTCHA, and limiting attempts, LoginPress bundles these powerful add-ons together. It shines as the best WordPress brute force protection plugin because it provides all necessary defenses in a single plugin.
This combination results in fewer plugin conflicts and a smoother user experience. This will allow you to enforce WordPress security best practices with minimal effort. Here are some ways LoginPress is a proactive security plugin:
- The Limit Login Attempts Add-On dashboard makes monitoring user login activity simple. You receive real-time logs that show you exactly which IP addresses are failing to log in, as well as which usernames are attempting to log in repeatedly.
This real-time monitoring enables the plugin to automatically block repeated login attempts or allow admins to blocklist them manually.
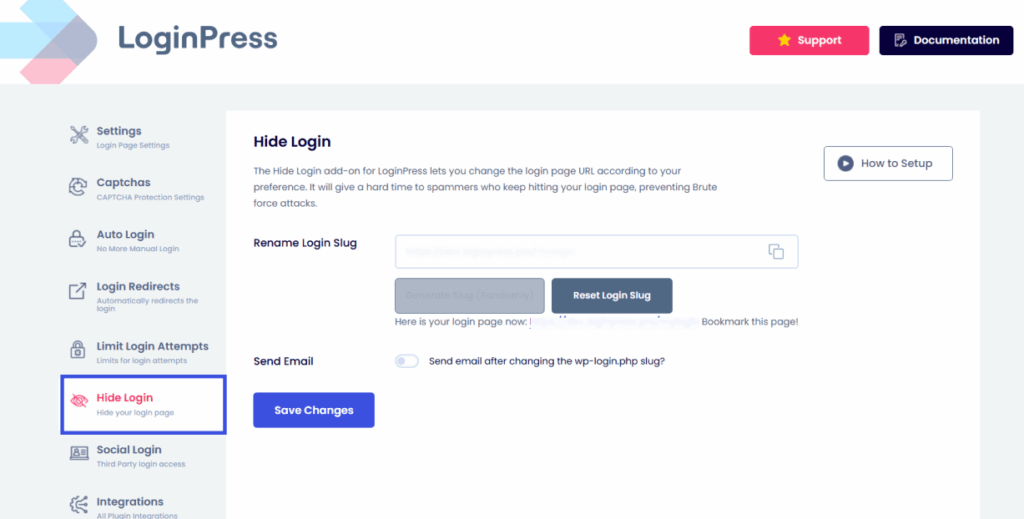
- LoginPress Hide Login Add-On allows you to hide wp-login URL for security to deflect casual bots. It also offers to send you an email later so you can save your changed URL.
- The CAPTCHA settings available in LoginPress enable you to add any CAPTCHA to your login forms to prevent bots from bypassing or from WordPress brute force attacks.
- LoginPress’s Social Login option allows your users to login using any social account for a smooth login experience, ensuring a great passwordless authentication method enforcement.

By offering top-notch security features in a single, user-friendly interface, LoginPress removes the technical hurdle, allowing every WordPress user to achieve professional protection.
Advanced Security Tips for WordPress Login
While limiting attempts and hiding your login page are the strongest defenses against WordPress brute force attacks, implementing proper WordPress security best practices requires a few additional tips to ensure a strong foundation.
- Harden the Database Prefix: A quick win for security is changing the default WordPress database prefix (usually wp_). Attackers use automated scripts that assume this default prefix when executing SQL injection attacks. Changing it to a unique, random string (e.g., wp_r9d4g7_) makes it much harder for these scripts to target your database tables.
- Disable or Limit XML-RPC: The xmlrpc.php file, used for remote publishing, has become a common point of exploitation for brute force attacks due to its multi-call function. In that case, I strongly recommend disabling them entirely by adding a simple command to your site’s configuration or using LoginPress’s Disable XML RPC Request option. If you must keep it, use tools to limit its access.
- Use Server-Side Protection (.htaccess): The .htaccess file (for Apache servers) is a native security tool that provides enhanced protection. You can also set up basic Web Application Firewall (WAF) rules. This layer of protection occurs before WordPress even loads, making it extremely fast and effective at blocking known malicious requests.
- Regular Updates and Backups: Reports show that 38% WordPress sites run on outdated software, creating an easy target for hackers. Most brute force attacks exploit known flaws in old plugins or themes, making immediate updates your topmost security priority.
Quick Ways to Handle a Brute Force Attack
According to a study, 60% of companies that suffer a cyber-attack are out of business within six months. Therefore, despite all precautions, a highly targeted or intelligent attack may still compromise your server. It is vital to be aware of the signs and take immediate action, as they can prevent damage to your site.
Signs of WordPress Brute Force Attacks
Here are key signs that you might be experiencing during a WordPress brute force attack:
- Extreme Server Slowness: Your site suddenly becomes very slow, often timing out or serving errors, due to the sheer volume of login requests overloading your server.
- Email Spam: Your inbox is flooded with notifications about “failed login attempts” (if you have them enabled).
- Unusual Traffic Spikes: Your hosting analytics show a massive, unexpected spike in traffic, almost entirely directed at your login page.
- Error Logs: You see constant, repeated database errors related to login failures in your server or WordPress logs.
Immediate Actions to Take
If you confirm that WordPress brute force attacks are happening, and you detect any of the signs mentioned above, take immediate action. Here are some initiatives you can take to protect your site from any serious damage:
- Block Malicious IPs: If your security plugin hasn’t automatically blocked the primary attackers, you may need to do it manually. That is where LoginPress provides proactive monitoring of your logs to identify suspicious IP addresses. You can also manually add them to your permanent block list.
- Reset Admin Passwords: Immediately force a password reset for all administrative users. Choose extremely long, random passwords.
- Check for Backdoors: If the attack successfully gained access, check your user list for any new, unauthorized admin accounts created by the hacker and delete them immediately.
- Inform Your Host: Contact your hosting provider. They can often implement firewall rules at the server level to block large traffic surges or known malicious IP ranges, protecting your resources.
How LoginPress’s Proactive features Assist in Recovery:
The automatic blocking feature in LoginPress acts as your first responder, often suspending the threat before you even notice. The easy-to-navigate logs table also simplifies the recovery process after WordPress brute force attacks by instantly showing you the compromised IP addresses you need to block.
You can find more information in this guide on How to Monitor and Analyze WordPress User Login Activity.
FAQs About Brute Force Protection
Does hiding my login URL completely stop brute force attacks?
No, but it stops the vast majority (often 99%) of automated, generic bot attacks. For the highest security, you must combine hiding the URL (using LoginPress) with limiting attempts and using CAPTCHA.
Does a login attempt monitoring plugin slow down my site?
Modern WordPress brute force protection plugins, such as LoginPress, are highly optimized. They have a negligible impact on performance compared to the severe performance drop caused by an actual, unmitigated brute force attack.
Is it safe to use “admin” as a username if I have a strong password?
I strongly recommend against it. Hackers already know the “admin” username, which means they only need to guess the password. Using a unique, custom username eliminates 50% of the guessing game for the attacker.
Should I block entire countries if they are the source of attacks?
You can, but only do this if you are sure you have no legitimate customers or traffic from that region. Blocking entire areas (also known as geo-blocking) can prevent genuine users from accessing your site. Focus on blocking specific, repeat offender IP addresses first.
WordPress Brute Force Attacks: Recap
The threat of WordPress brute force attacks is a constant reality, but it doesn’t have to be a source of stress. The solution isn’t complex code; it’s a simple, layered defense strategy applied consistently.
By implementing the three core methods, such as limiting attempts, hiding your login URL, and using CAPTCHA, you immediately upgrade your security status to a professional standard.
With the help of tools like the LoginPress WordPress login form plugin, you can simplify this process without needing to be a security expert.
So don’t wait until a successful attack disables your site, damages your reputation, and compromises your data. The tools are ready for login attempt monitoring in WordPress, the setup is easy, and the peace of mind is priceless.
If you’re ready to take the next step and optimize your checkout process, I recommend exploring our recent guide on WooCommerce Login Security: Complete Guide (2025) to see how else you can optimize your login form.
Also, check out more related articles:
- WordPress Login Security: 13 Ways to Secure Login Page
- How to Customize WooCommerce Login and Registration Forms
So, are you ready to protect your site from constant brute force attacks? Let us know in the comments which method you found the most helpful!



