15 Most Common WordPress Security Issues (Solved)
Do you want to know about the most common WordPress security issues along with their possible solutions?
WordPress websites are frequent targets for cyberattacks, which may lead to a range of security threats, such as brute force attacks. But don’t worry, we’ve got you covered.
In this guide, we’ll cover 15 of the most common WordPress security issues with solutions to help you keep your site safe and secure.
WordPress Security Issues (TOC):
Why is it Important to Secure Your WordPress Site?
WordPress is a popular open-source content management system (CMS). It allows users to easily create, manage, and publish sites without requiring advanced coding skills.
WordPress is secure, but it can only be protected if appropriately maintained. Therefore, it is recommended that you manage it properly.
Here is why you might want to secure your WordPress site:
- Protection from Hackers and Malware: Securing your site helps prevent attacks that can lead to data breaches.
- Safeguarding User Data: Most WordPress sites gather user information, such as emails, which can be stolen if the site is hacked. By securing your site, you ensure your users’ privacy.
- Preventing Website Downtime: If you keep your WordPress site secure, it minimizes the risk of downtime due to attacks.
- Protection from Spam and Phishing: Securing your site protects your site from spam or phishing emails.
- Preserving Your Reputation: A hacked WordPress site can damage your site’s brand reputation. So, you can save from it simply by securing it well on time.
Securing your WordPress site is a proactive way to protect your business and online presence.
15 Most Common WordPress Security Issues (Solution)
1. Outdated WordPress Core, Plugins, and Themes
WordPress empowers 43% of all sites on the internet, including blogs, business sites, online stores, and more. This is what makes it a prime target for cybercriminals. They keep trying bots, brute force attacks, and other security attacks to take control of your site.
Outdated WordPress core, plugins, and themes are common security vulnerabilities that hackers can use to exploit your site.
This is why WordPress keeps sending updates with bug fixes, addressing unexpected CSS specificity changes in themes, and more. It minimizes the chances of your site getting hacked.
So, it’s better to regularly update your WordPress core, plugins, and themes to the latest versions.
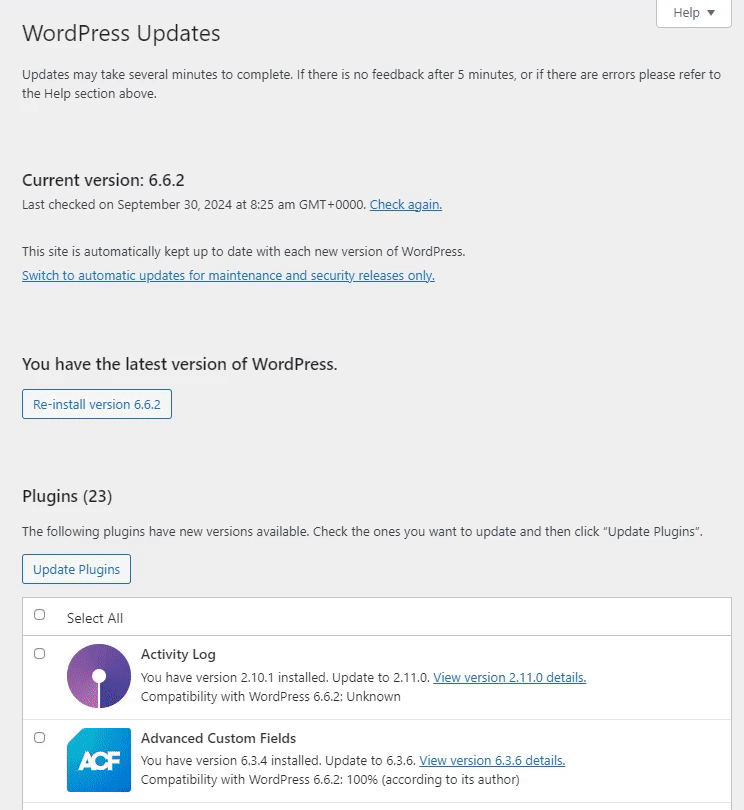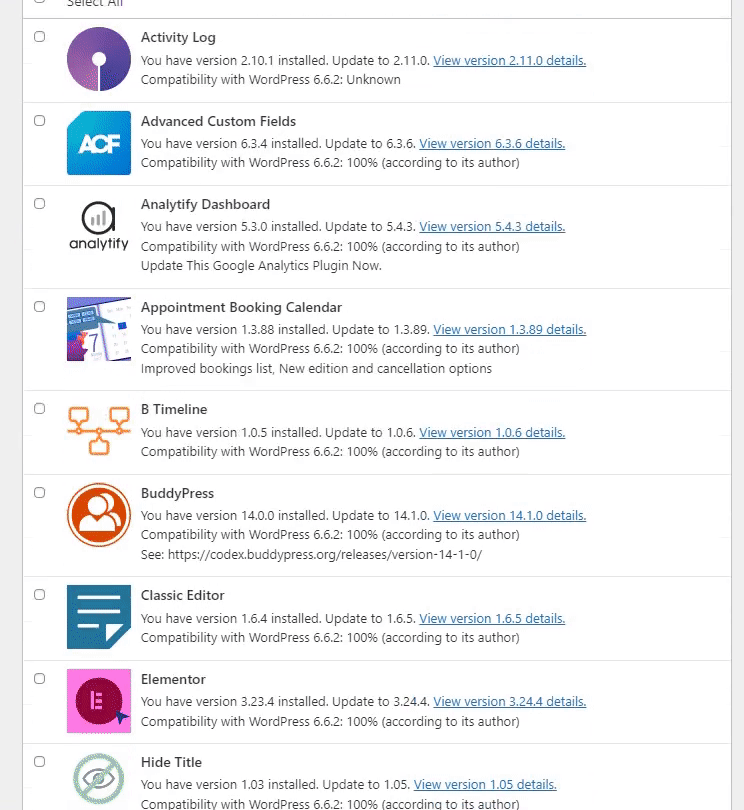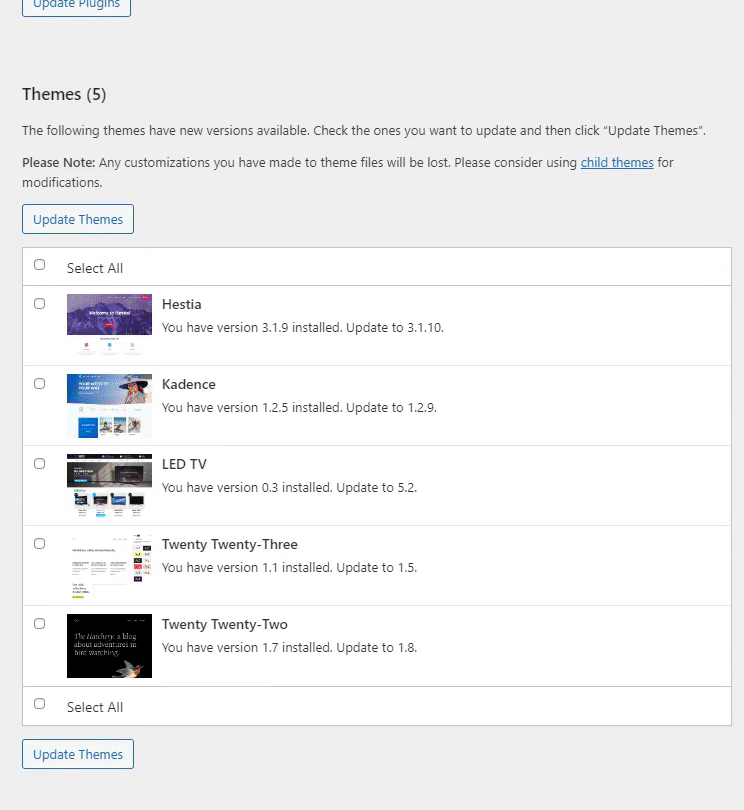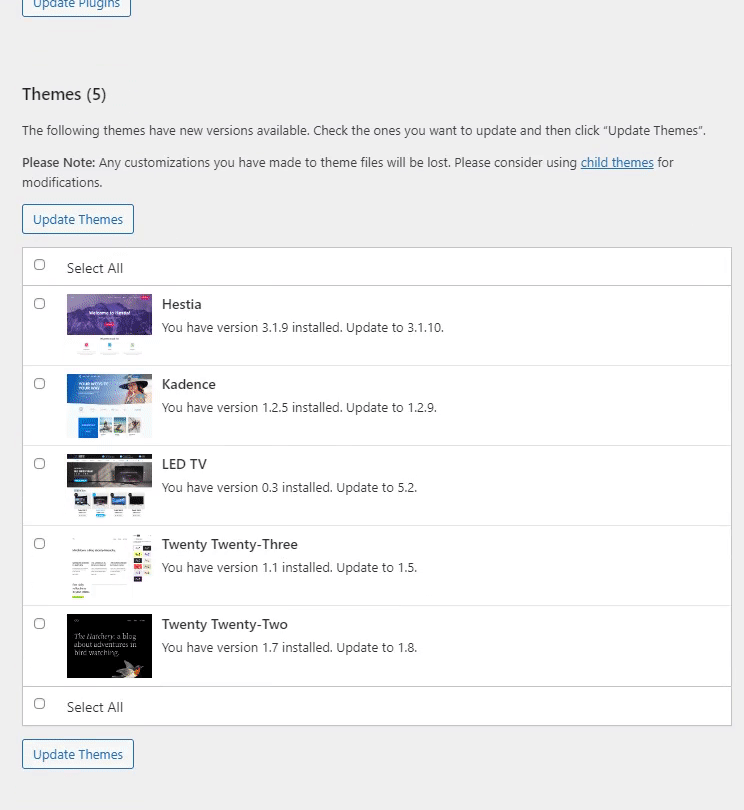
All you need to do is go to the left sidebar of the WordPress admin dashboard, navigate to Dashboard, and click the Updates option.
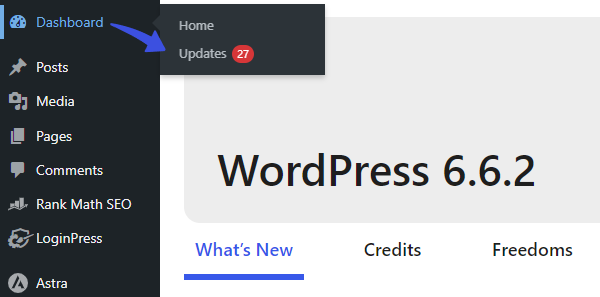
On the next screen, you’ll find all the options to update the WordPress core, plugins, and themes.
See the GIF below:
2. WordPress Login Security
WordPress’s login page serves as the gateway to your site. You need login credentials, i.e., Username, and Password, to get access to the site.
This is why improving login security is required to control hackers. It is the first defense against unauthorized access to your website or online accounts.
This is where the best WordPress login plugin, LoginPress comes into play. It offers everything to strengthen the default WordPress login, register, and forget pages.

Secure Your WordPress Login
Stand out from the competition with the best WordPress login plugin that lets you strengthen your login page – no coding required!
Let’s find out some key points about login security in WordPress and how LoginPress assists you in them:
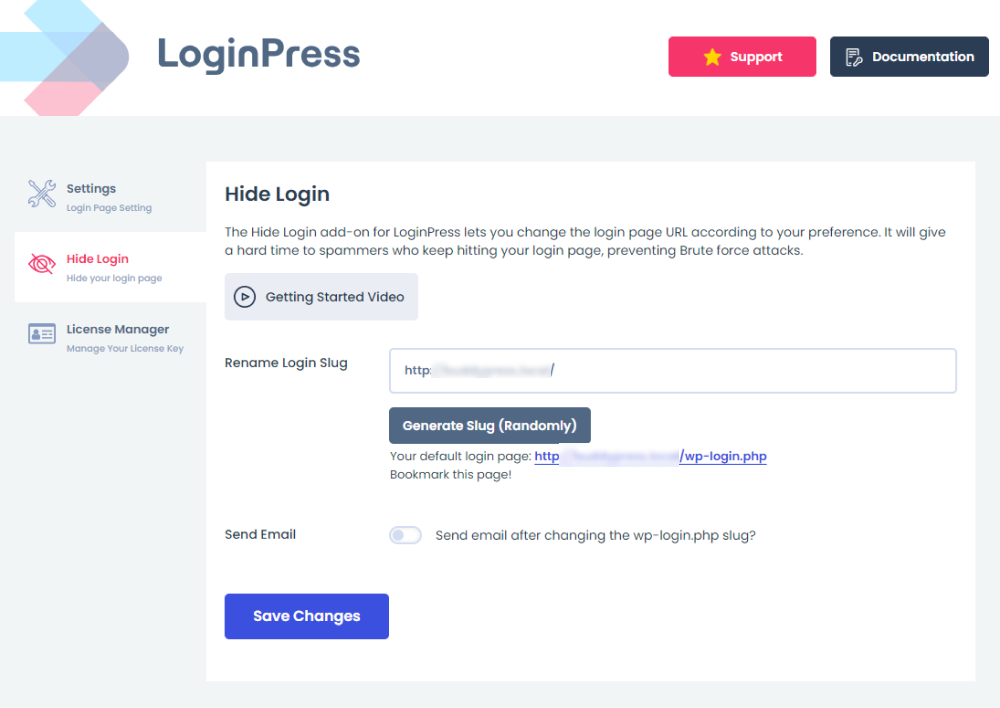
- You might know that the default WordPress login URL is wp-admin or wp-login.php. A hacker can reach your login page simply by guessing your domain name.
So, it’s better to change the default login slug with something only you know. The LoginPress Hide Login Add-on makes this easy.
Note: You’ll need LoginPress Pro installed and activated on your site. After that, activate the LoginPress pro key.
See the image below:
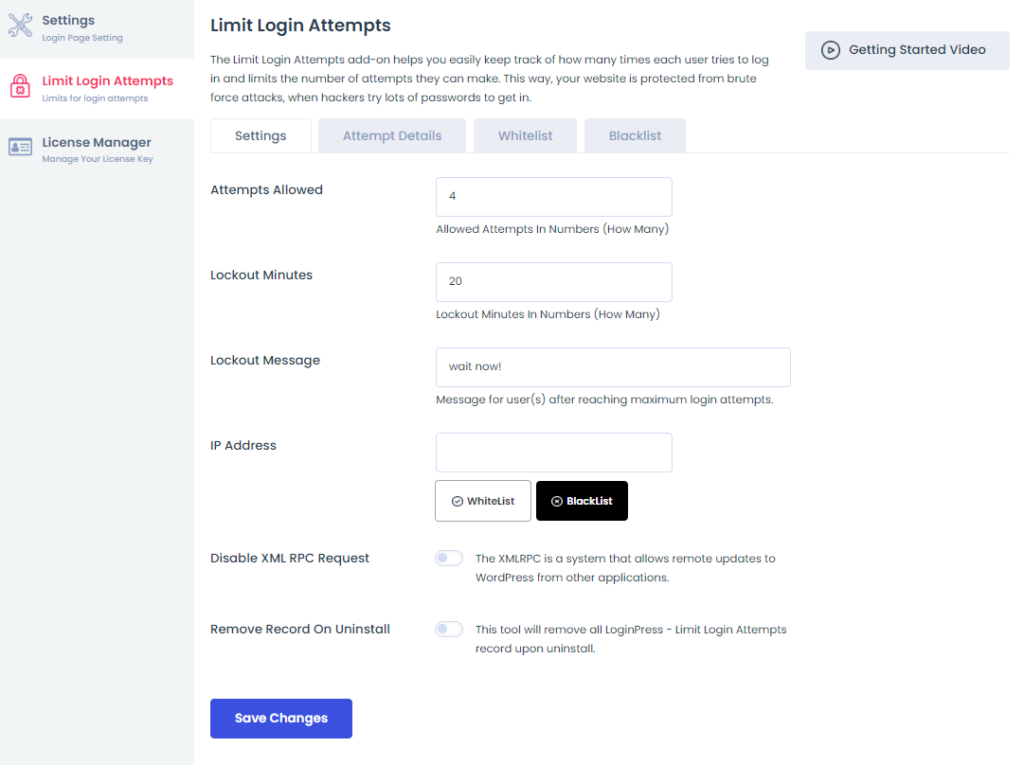
- By default, WordPress doesn’t limit login attempts. Hackers take advantage of this and keep guessing the login credentials, and sometimes they succeed.
So, as a general rule, it is a good practice to limit login attempts with the LoginPress Limit Login Attempts Add-on.
It allows you to set a limit on the login attempts. You can keep track of all the login attempts and whitelist or blacklist them.
See the image below:
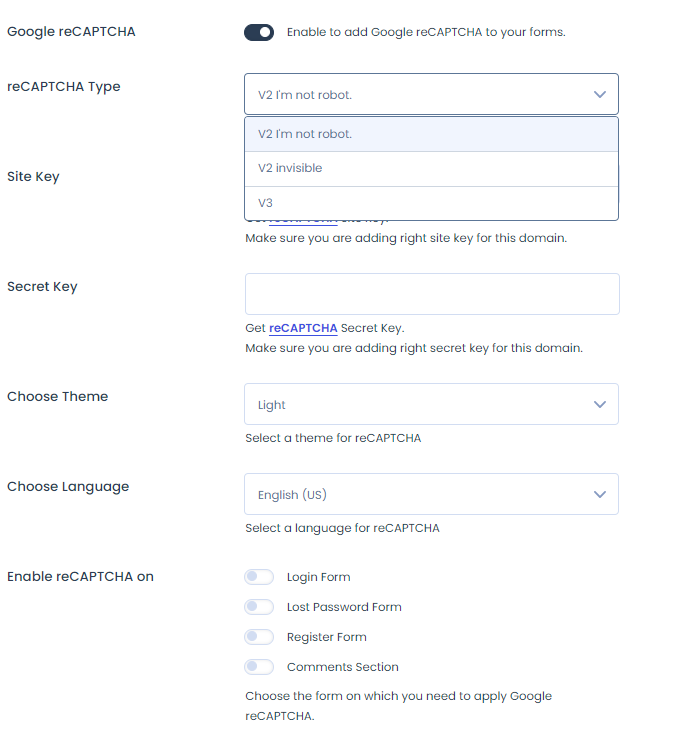
- LoginPress reCAPTCHA lets you add V2 I’m not a robot, V2 Invisible, and V3 reCAPTCHA type to the login, lost password, register, and comment section of your WordPress site to protect it from bot attacks.
See the image below:
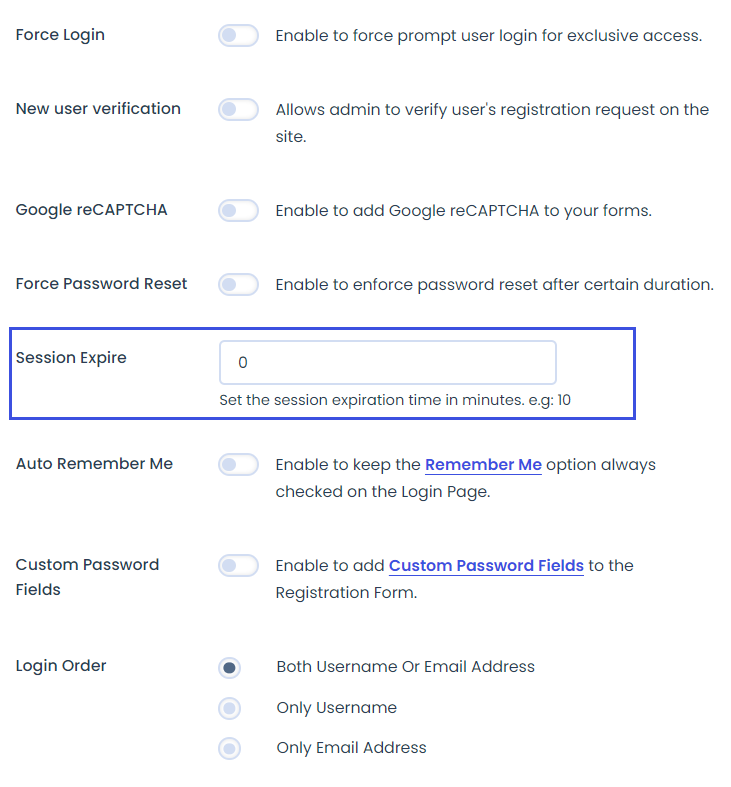
- By default, WordPress sessions expire after 48 hours. However, if you are logged in to your site and remain inactive for 48 hours, you will remain logged in.
This is a risky state as hackers can hijack your site during this time. The LoginPress Session Expire feature fills in the gap nicely.
See the image below:
3. Brute Force Attack
A brute force attack is one of the most common WordPress security vulnerabilities. In this attack, hackers repeatedly attempt to guess your login credentials until they can crack the code and break in. Once they are in, they’ll take control of everything.
In unauthorized login, the attacker mostly uses brute-force attacks to get access to a site’s WordPress admin area.
The attackers use a bot to try a combination of billions of usernames and passwords.
Since there is no limit on login attempts, they guess the right credentials, i.e., username and password.
You can avoid this type of WordPress security issue by using strong passwords, limiting the number of login attempts, and enabling two-factor authentication (2FA). Security plugins can also monitor login attempts and block suspicious activity.
Other than this, you can strengthen your password.
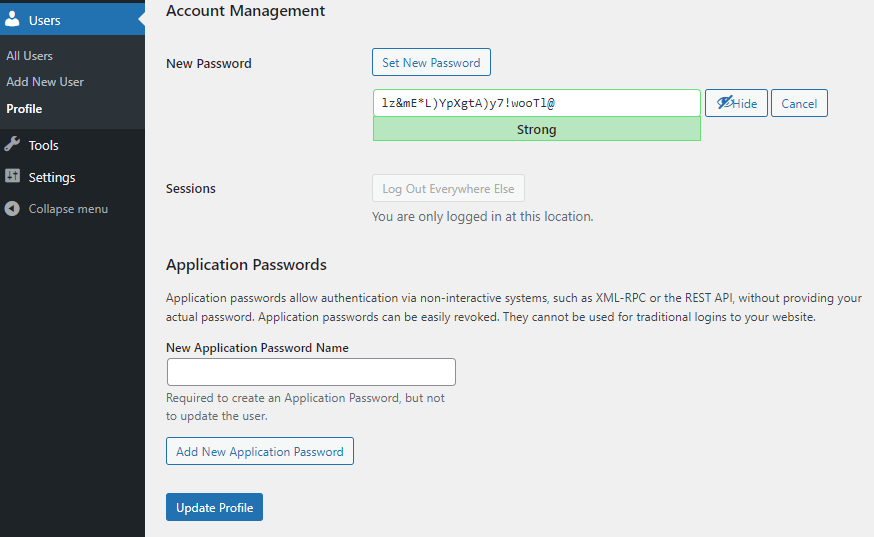
To do this, go to the left sidebar of the WordPress admin dashboard, navigate to Users, and click the Profile option.
On the next screen, create a strong password.
Note: You can create a new password on your own or use Strong Password Generator for creating a complex
See the WordPress account management screen:
Note: It is a good practice to update your password every six months. You can also Limit login attempts and use two-factor authentication (2FA). Install plugins like Limit Login Attempts or use reCAPTCHA on your login page.
4. Malware
Malicious software can infect your site, leading to data theft or a compromised site.
Hackers use multiple malware to damage your WordPress site, such as:
- Malicious redirects
- Drive-by downloads
- Backdoor attacks.
These attacks are usually carried out through security defects/vulnerabilities in WordPress core, plugins, or themes, and over-privileged (i.e., admin) to a lower privilege level(such as Editor or Author), and more.
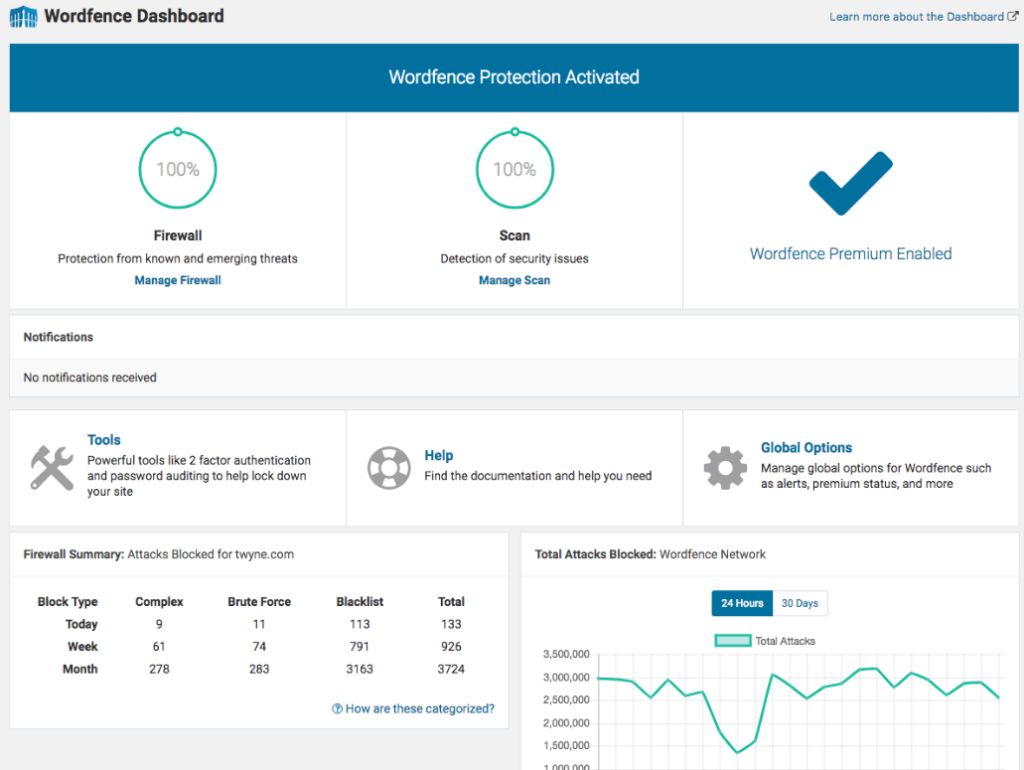
To save your site from such attacks, you can install and activate a WordPress malware scanner plugin, such as Wordfence, for your site.
This plugin helps you to:
- Scan WordPress core files, themes, and plugins for malware
- Checks bad URLs
- SEO spam,
- Malicious Redirects
- Code injections.
5. DDoS Attacks in WordPress
A distributed denial-of-service (DDoS) attack is a type of attack built to force a WordPress site. It accomplishes this by flooding a server with traffic. As a result, site administrators and visitors need access to your site, making it unavailable.
This attack causes downtime and hurts your site’s overall reputation.
Note: These attacks usually target a site with poor hosting security. Therefore, you should always choose the best hosting provider. If you need help, see our detailed guide on 11+ Best WordPress Hosting Providers 2024.
To protect against DDoS attacks, use a content delivery network (CDN) like Cloudflare, which offers DDoS protection.
Note: See our detailed guide on 9 Best CDNs for WordPress in 2024 (Compared).
6. Phishing
Phishing is another WordPress security concern in which hackers send users emails, text messages, phone calls, etc., to trick users into giving up sensitive data, such as:
- Usernames
- Passwords
- Credit card numbers
- Bank account information
See the image below:
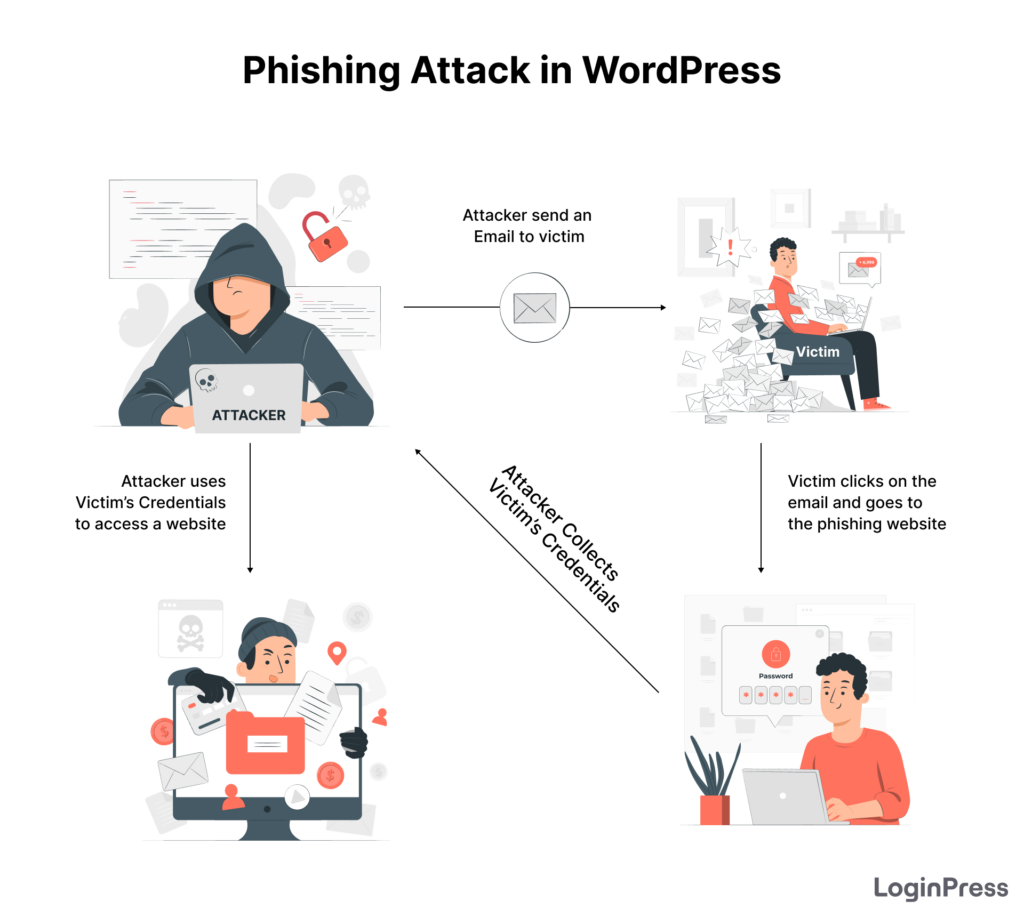
Most of the time, hackers prompt the user to do something, like updating their password.
If you fall victim to this, your site’s security will be compromised.
To save your WordPress site from falling victim to phishing, you’re required to take some security measures on your part, such as:
- Avoid clicking every link
- Don’t provide login credentials to unsecure
- Ignore popups
- Don’t open suspicious documents
Other than this, it’s better to go for WordPress anti-phishing solutions to keep track of all the phishing attempts.
7. Poor Hosting Provider
A poor hosting provider can be a significant security issue for WordPress for several reasons:
- Outdated Server Software: Outdated server software, such as PHP, MySQL, Apache, etc., that hackers can use to exploit and compromise your WordPress site.
- Weak Security Protocols: A poor hosting provider needs firewalls, malware scanning, and DDoS protection. As a result, your WordPress site might face brute force, SQL injections, or malware.
- Shared Hosting Risks: A low-cost hosting provider offers shared hosting plans. If one site on the server is compromised, it can put other sites at risk.
- Lack of SSL Support: Low-quality hosting providers may not offer easy integration of SSL certificates.
- Unmonitored Security Logs: Security logs help track your site’s threats, unauthorized access, and suspicious activities. However, a poor hosting provider neglects this, making it easier for attackers to attack your site.
You can solve this issue simply by choosing a reputable hosting provider with security features, such as firewalls and automatic backups.
8. Undefined User Roles
Undefined user roles can also be a common cause of WordPress security issues.
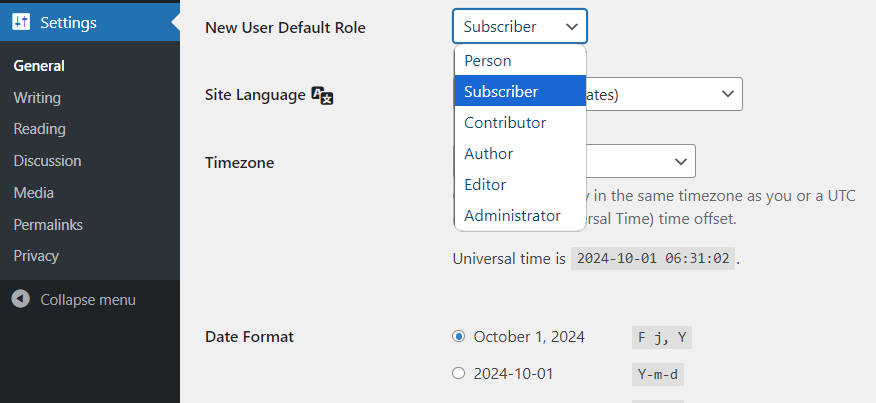
As you know, by default, WordPress offers six user roles to assign to individuals as per their role on your site, including:
- Administrator (they can do everything on a site)
- Editor (can gain access to each post, page, comment, etc., and can upload media.)
- Author (has the right to write, upload media, i.e., images, videos, etc., edit, and publish posts.)
- Contributor (cannot publish/upload anything. They can only write and edit their posts when published.)
- Subscriber (one who subscribes to your updates.)
- Person (they can read and comment on posts and pages on private sites.)
See the image below:
As a general rule, you should audit and manage user roles regularly. For this purpose, you can use a WordPress plugin like User Role Editor.
You Might Also Like: How To Exclude Specific User Roles From The Session Expiration
9. Misconfigured WordPress Database
A misconfigured WordPress database is another security issue because it can expose sensitive data and make your WordPress site vulnerable to attacks.
Here are the key reasons why:
If the database is not configured correctly with strong access controls, unauthorized users (including hackers) can gain access to sensitive information, such as:
- Usernames
- Passwords
- Email addresses
This can lead to identity theft, data breaches, and other malicious activities.
A misconfigured WordPress database may need proper security measures to prevent SQL injection attacks. Correct configuration and regular security audits are essential to minimize vulnerabilities.
10. Structured Query Language (SQL) Injections
Structured Query Language (SQL) Injections are one of a site’s most common WordPress security issues.
WordPress stores all information, including user data, post content, settings, passwords, etc., in a MySQL database. With the help of SQL injection, attackers inject SQL queries into forms, URLs, etc., which the server executes. This can give attackers access to sensitive data like usernames, email addresses, or passwords.
Once they are in, they can use SQL injections to modify database entries, i.e., changing content on your site. For example, an attacker could replace homepage content by injecting links to phishing sites.
To save your site from falling victim to SQL injections, you can use WordPress security plugins like Wordfence or Sucuri. They can detect and block SQL injection attempts.
Other than this, you should keep WordPress core, themes, and plugins updated. In addition, you should always download themes and plugins from trusted sources.
11. Search Engine Optimization (SEO) Spam
Top-ranking WordPress sites often attract hackers’ attention. They inject spammy links or content into an existing article, create a new page, etc., filling it with strange content, malicious links, and even spam malware.
Here are some common signs of SEO spam:
- Links to unrecognized sites
- Seeing pages and content on your site
- Multiple redirects to other sites from your site
- Unusual ranking metrics
- Content in a different language
You can save your site from these kinds of threats simply by using tools like Google Search Console or anti-spam plugins. These tools help scan your site regularly for spam content. You should also clean your database and keep plugins/themes updated.
12. Supply Chain Attacks
Supply chain attacks are one of the most increasingly common WordPress security issues for WordPress.
As you know, WordPress sites rely on third-party plugins and themes. They help users add desired functionality to their site.
A supply chain attack occurs when an attacker gains control of a plugin or theme and injects malicious code. They’ll fall victim once the admin updates or installs any of these infected plugins and themes.
For example, a popular plugin may be attacked, and users who trust it may install a version that contains malware.
Other than this, some supply chain attacks target hosting providers. If the hosting falls victim to them, it can lead to a supply chain attack. This is mostly dangerous for shared hosting because other sites will face the same if one site is affected.
To protect your site from such attacks, download plugins, themes, etc., from recognized sources, such as the official WordPress plugins and themes repository. In addition, you should perform timely updates, security audits, and backups.
13. Cross-site Request Forgery (CSRF)
Cross-site Request Forgery (CSRF) is another prominent WordPress security issue. It exploits a site’s trust in a user’s browser.
WordPress security issues occur when a malicious site or email unknowingly convinces a logged-in user to submit a request to another site.
When they are in, they unknowingly perform actions, such as:
- Changing settings
- Publishing posts
- Deleting content
For example, an attacker sends the user a link or embeds a form on a malicious site. When the user clicks the link or the form submitted, the attacker sends a request, i.e., publishing a post, to the target WordPress site where the user is logged in.
WordPress will consider the request legitimate since the user has already been authenticated on that site. This way, the attacker can use an innocent user to do what they want on the target site.
Use WordPress security measures like nonces (security measure) to protect against Cross-site Request Forged (CSRF).
In addition, the WordPress site’s admin should also ensure they use secure, updated plugins and limit user privileges to reduce such risks.
14. Hotlinking
Hotlinking is another common WordPress security issue when another site directly embeds or displays media files, such as images, videos, etc., without your permission.
Initially, it doesn’t seem like a security issue, but it can later create several problems for your site. For example, it may affect a site’s security, performance, etc.
You can safeguard your WordPress site’s resources, reputation, and suitable security measures.
For example, you can disable hotlinking through your server settings, e.g., Apache, Nginx, or use All In One WP Security & Firewall plugins to block hotlinking.
15. Insufficient Monitoring of User Logins and Activities
Insufficient monitoring of user logins and activities is one of the most common WordPress security issues that can raise WordPress vulnerabilities, including
- Brute force attacks
- Account compromises
- Insider threats.
You cannot detect suspicious behavior if you don’t track user logins and activities on your site. Consequently, you’ll fail to take action before severe damage occurs.
Note: See our detailed guide on How to Monitor and Analyze WordPress User Login Activity.
Let me describe a scenario for you here. A hacker inside your site can install malicious plugins, edit themes, steal data, or modify files without your knowledge.
If user activities are logged and monitored, it becomes easier to trace the changes and who made them. So, it becomes way more complicated to recover and secure the site.
Consequently, the attacker can compromise the site further,
Activity logs can help you spot suspicious actions quickly, such as tracking users logging in from unfamiliar locations or IP addresses.
Install an activity log plugin like WP Activity Log or Simple History to protect your site from security issues. This helps monitor login attempts, role changes, or content modifications.
WordPress Security Issues FAQs
What is a brute force attack, and how can I prevent it?
A brute force attack involves trying many username-password combinations to gain access to your site. Prevent it by limiting login attempts, using 2FA, a strong and complex password, and implementing a reCAPTCHA on your login page.
Are WordPress themes and plugins secure?
Most WordPress themes and plugins are secure. You should use them from reputable sources, such as WordPress.org, and keep them updated. It is also always a good practice to check reviews and update logs before installing and activating them on your site.
How can I protect my WordPress login page?
You can easily protect your WordPress login page with a plugin like LoginPress. It has everything to protect your login page. You can change the default login UR with LoginPress Hide Login Addo-on, limit the number of login attempts with LoginPress Limit Login Attempts Add-on, add Session Expire Time, and much more.
How do I know if my WordPress site has been compromised?
You can quickly know if your WordPress site has been hacked. Common signs of a compromised site include unexpected changes to content, website redirects or pop-ups, slow site performance, unauthorized admin users, and warnings from Google or browsers.
What should I do if my WordPress site gets hacked?
If your site is hacked, you can restore a backup, scan your site for malware using a security plugin, change all passwords, and check for suspicious users or content. You can also contact your hosting provider for assistance if necessary.
How vital are backups for WordPress security?
Backups are essential for your site. If your site is hacked, you can restore it to a clean state if you have a backup.
Final Thoughts
To sum up, we’ve addressed 15 common WordPress security issues. Knowing about them can reduce the chances of vulnerabilities and enable you to take preventive measures.
Remember, security is not a one-time task but an ongoing process. So, it is better to update, backup, and monitor your site regularly.
That’s all for this article!
Here are the key takeaways:
- Outdated WordPress Core, Plugins, and Themes
- WordPress Login Security
- Brute Force Attack
- Malware
- DDoS
- Phishing
- Poor Hosting Provider
- Undefined User Roles
- Misconfigured WordPress Database
- Structured Query Language (SQL) Injections
- Search Engine Optimization (SEO) Spam
- Supply Chain Attacks
- Cross-site Request Forgery (CSRF)
- Hotlinking
- Insufficient Monitoring of User Logins and Activities
You can also check out our other articles, such as Top LoginPress Addons To Boost Your WordPress Login Experience and WordPress Security Audit: Updated Checklist (2024).